34+ precedence diagram method examples
The source code used in all 101 examples as well as possible list of errata can be found on the Facebook page of this book. The articles identified in this scoping review assessed a wide range of outcomes.

Aon Activity Node Precedence Diagram Edrawmax Editable Template Diagram Activities Dichotomous Key
Finish to finish FF.

. A substrate layer providing step of providing a substrate layer. This seminar will show you how to perform a confirmatory factor analysis using lavaan in the R statistical programming language. 4 4 6 6 6 7.
Scope and limitation 05. The DMADV development is linear but in reality it needs to be iterative due to the complexity of most projects. All four values are predictable considering the inheritance logic in the above diagram.
To lay on the. INTRODUCTION The Transmission Control Protocol TCP is intended for use as a highly reliable host-to-host protocol between hosts in packet-switched computer communication networks. A technique to create project schedule network diagrams is the precedence diagramming method which we are explaining in this article incl.
129 124 112 81 55 44 40 27 21 5 TRANSMISSION CONTROL PROTOCOL DARPA INTERNET PROGRAM PROTOCOL SPECIFICATION 1. A Uniform Resource Identifier URI is a unique sequence of characters that identifies a logical or physical resource used by web technologiesURIs may be used to identify anything including real-world objects such as people and places concepts. The motions which shall be received under Rule XXII when a question is pending and which shall have precedence as they stand arranged are.
Fifty-four studies assessed production. Python Quick Guide This Python tutorial is for beginners which covers all the concepts related to Python Programming including What is Python Python Environment Setup Object Oriented Python Lists Tuples Dictionary Date and Times Functions Modules Loops Decision Making Statements Regular Expressions Files IO Exceptions Classes Objects Networking and GUI. To take a recess.
One of the main disadvantages of the DMADV method is that its implementation takes precedence over creativity and innovation. The 4 types of dependencies are. Astropyunits handles defining converting between and performing arithmetic with physical quantities such as meters seconds Hz etc.
It also handles logarithmic units such as magnitude and decibel. Of these studies 10 collected primary data through surverys and interviews 10 studies used both primary and secondary data and the remaining 34 studies analyzing secondary data. To adjourn to a day certain or that when the Senate adjourn it shall be to a day certain.
Consider the hash table size be 10. Enter the email address you signed up with and well email you a reset link. If you want to deal with celestial coordinates see the astropycoordinates package.
Fallback values are the second argument used in the var function which denotes the substitution of a CSS variable. Displaying the. A method for manufacturing an environmental-friendly heat shielding film using a non-radioactive stable isotope includes.
Its emphasis is on understanding the concepts of CFA and interpreting the output rather than a thorough mathematical treatment or a comprehensive list of syntax options in lavaanFor exploratory factor analysis EFA please refer to A Practical. The diagram is based on and often enriched with information about the type of logical relationship between activities. DMADV needs to be agile and flexible in order to produce better projects.
And a heat shielding layer forming step of after the substrate layer providing step forming on one surface of the substrate layer a heat shielding layer containing a non-radioactive stable isotope tungsten. Many texts on HAC show the formula its method-specific views and explain the methods. Here we also discuss the algorithm of hash table in c along with different examples and its code implementation.
Astropyunits does not know spherical geometry or sexagesimal hours min sec. Creating computer programs and with examples given in this book writing computer programs would appear to be more realizable especially for beginners with absolutely no programming background. Among all the PMP Exam formulas calculation questions the Earned Value Management EVM questions are usually considered the most important ones as candidates will need to solve quite a few of them in the real PMP Exam I got around 5 EVM questions on my PMP Exam paper and I am quite confident that I could get them all correct.
Deleting element 34 from the hash table htdeleteElement34. The case studies and the examples in the study have been chosen as a generic representation of each category. We categorized the outcomes for clarity.
Method of the study. Depending on the linkage method the parameters are set differently and so the unwrapped formula obtains a specific view. Fallback Values In CSS Variables.
To proceed to the consideration of executive business. Let us understand this with the help of the diagram given below. I would recommend articles by Janos Podani as very thorough.
The recurrence formula includes several parameters alpha beta gamma.

Float Calculation Precedence Diagram Edrawmax Editable Template Diagram Dichotomous Key Templates

Project Management Youtube Project Management Projects Math Lessons
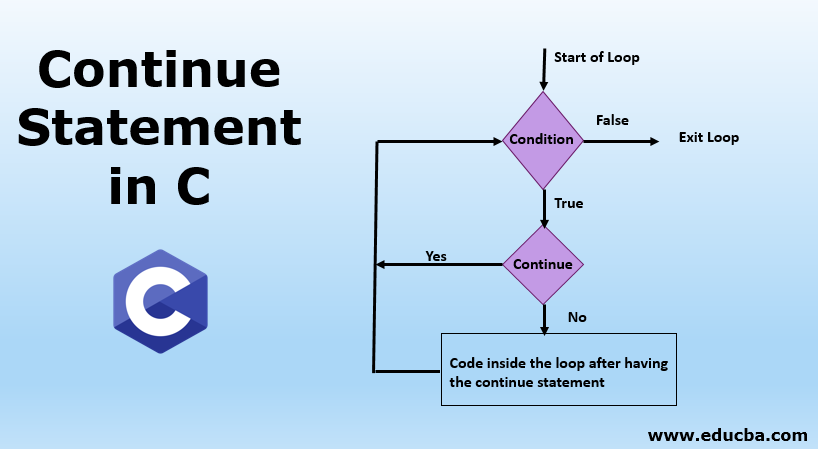
Continue Statement In C Syntax And Flowchart Examples With Code
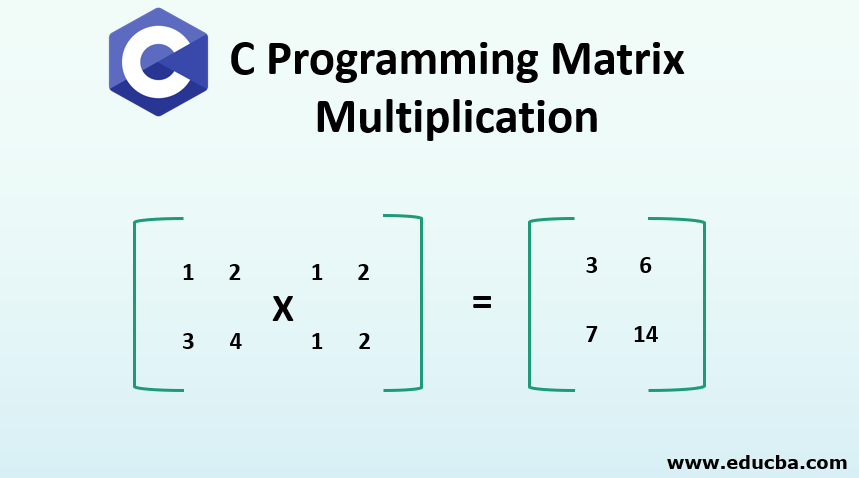
C Programming Matrix Multiplication C Program For Matrix Manipulation

Engineering Precedence Diagram Edrawmax Editable Template Diagram Templates Graphing

Precedence Diagram Method Edrawmax Editable Template Diagram Dichotomous Key Templates
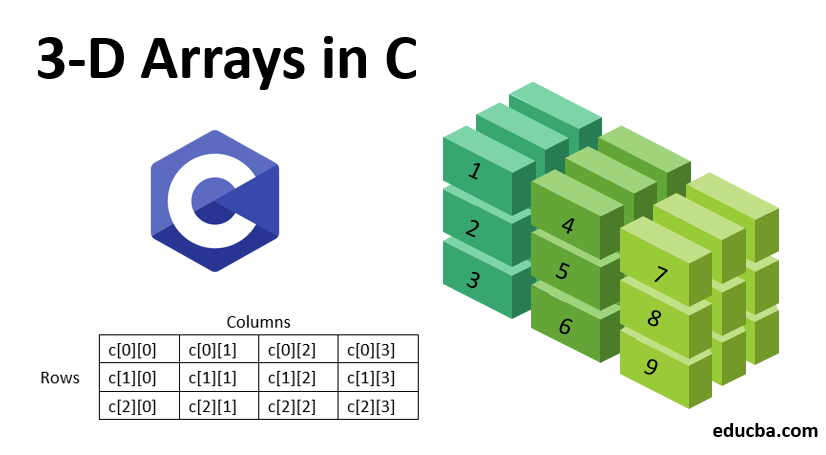
3d Arrays In C Learn The Initializing And Eements Of 3d Array
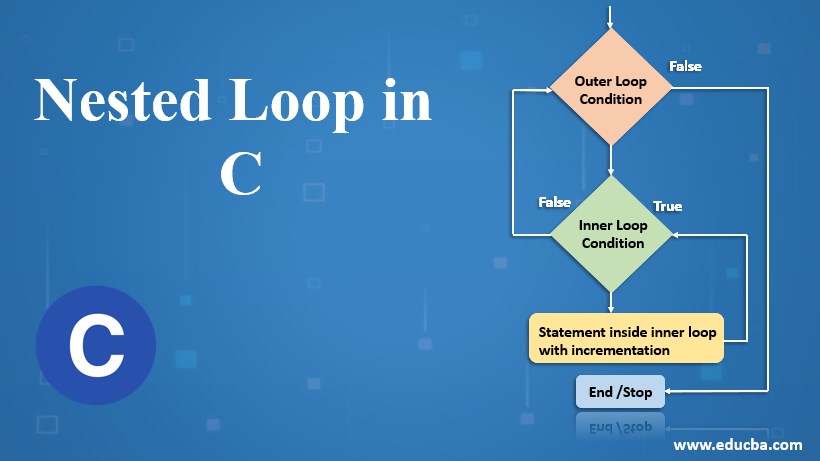
Nested Loop In C Examples To Create Nested Loop In C Programming

10 Interesting Flowchart Templates For Students Flow Chart Template Flow Chart Student
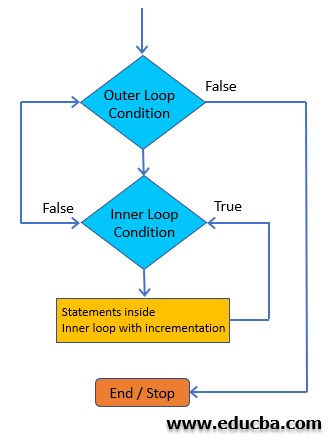
Nested Loop In C Examples To Create Nested Loop In C Programming

Precedence Diagram How To Create A Precedence Diagram Project Management Books Agile Project Management Diagram

Critical Path Analysis In A Precedence Diagram Analysis Stakeholder Mapping Sample Resume
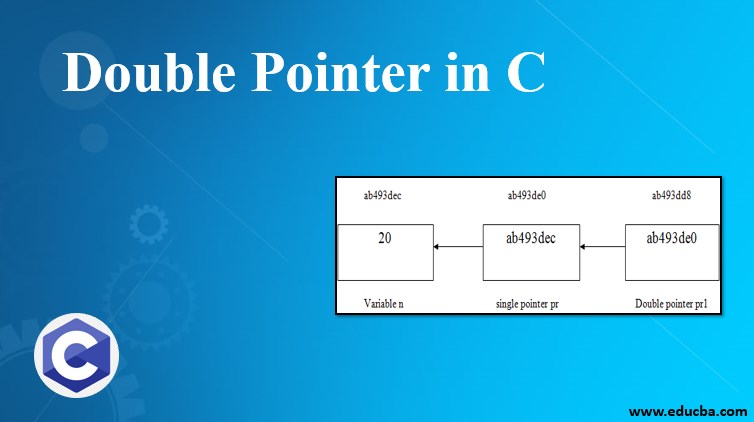
Double Pointer In C How Does Double Pointer Work In C With Examples
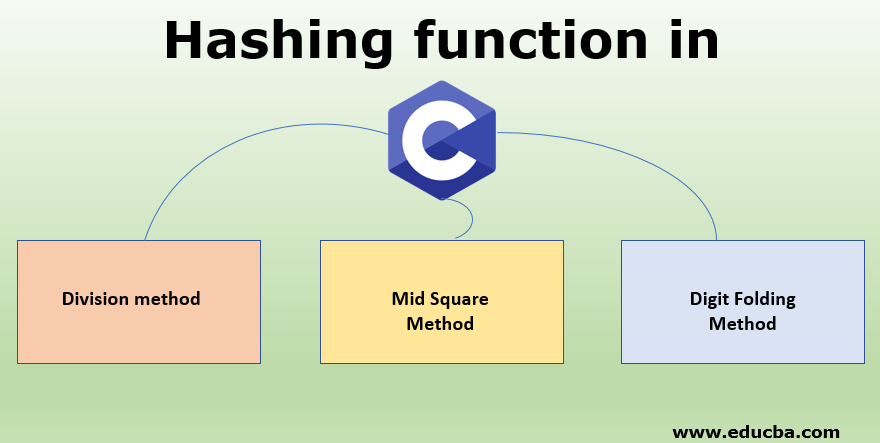
Hashing Function In C Types Of Collision Resolution Techniques
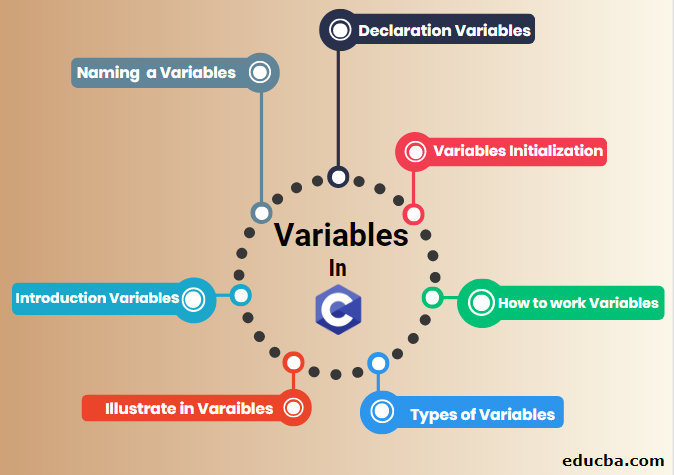
Variables In C How To Declare Initialize The Variable Types Examples

Aon Activity Node Precedence Diagram Edrawmax Editable Template Diagram Activities Dichotomous Key
Break Statement In C Syntax Flow Chart And Examples